Introduction
On 01/04/2022, I had the pleasure of organizing the Hacky'Nov event. As part of this event, I created 4 challenges. There were two web challenges and two programming challenges. Here, I will only detail the web challenges.
For more information about the event: https://hackynov.fr
Time To Plane
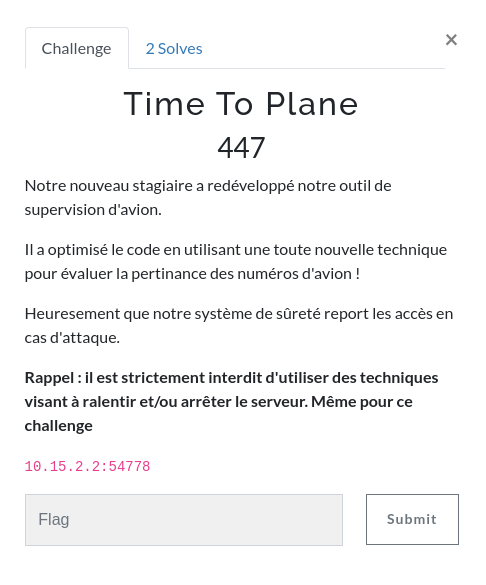
When you arrive on the page, you come across an airplane monitoring system. You can enter the flight number you want to monitor.
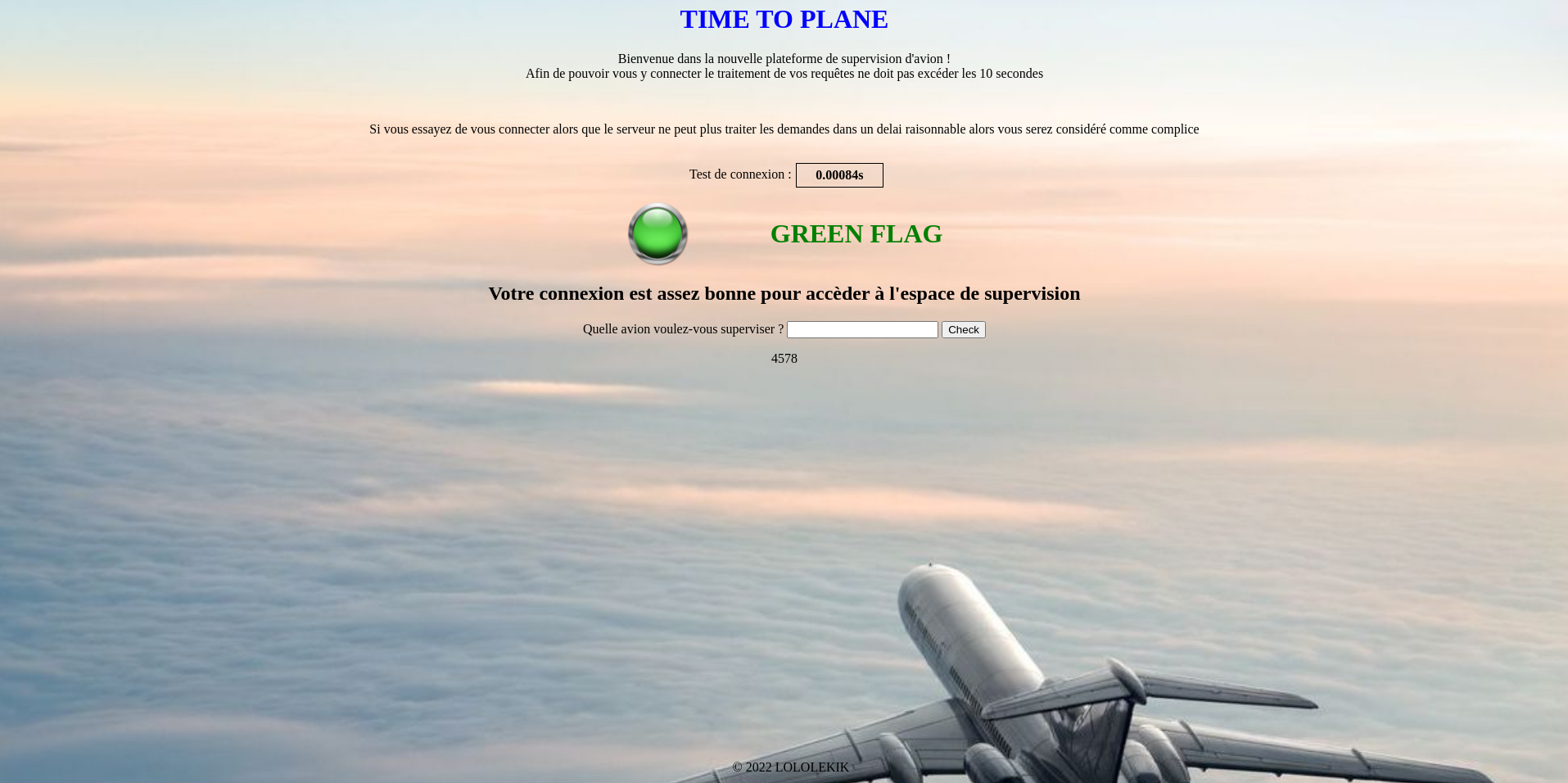
It quickly becomes clear from the message displayed that the goal is to crash the monitoring system. To do this, we start testing the characters we can use.
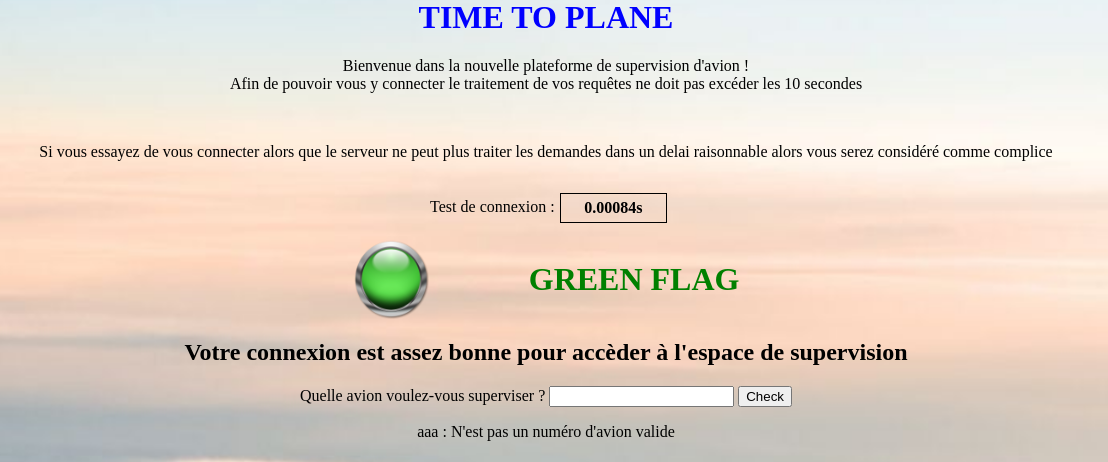
We see that letters are not recognized and that some special characters are recognized as an attack.

However, we see that when we use double parentheses, there is no error.

Looking at the site headers, we see that it is a Flask application, so it runs on Python.
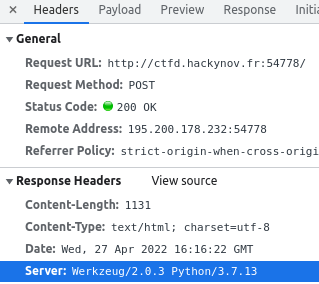
We might think that the "new technique for evaluating the relevance of flight numbers" is probably an eval function. So we try to inject some code.
payload = time.sleep(10)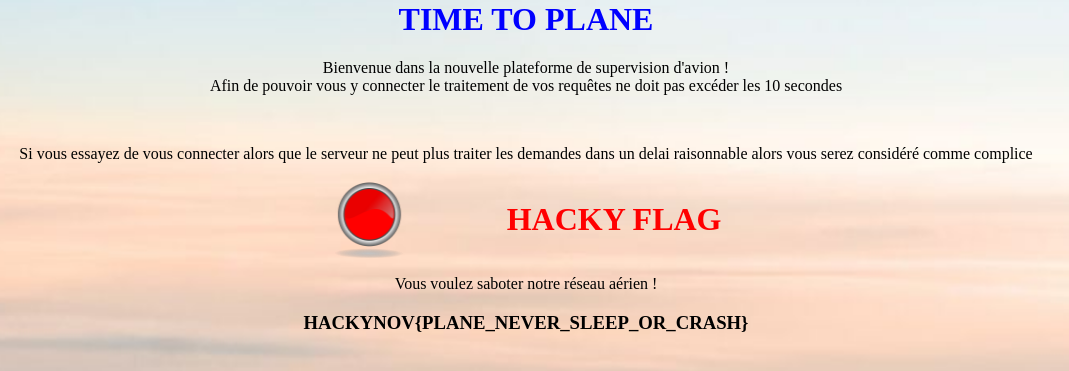
RECOAPP
Here is the page we land on.

By translating and playing around with the application, we understand that it is a tool that recognizes words in an image. The tool determines whether the word is considered good or bad. To test, we take a Word document on which we write:
test
test 1
test2
azertyuiop
By repeating the operation, we realize that the tool never gives the same "rating" to our word. We can consider that it is done completely randomly. We then use a list of special characters to detect abnormal behavior.
Example:
&
'
||
(
)
@
_
^
)
We see that some characters are interpreted but not displayed. We also see that only 4 lines are present.
We then try to chain a special character with a command to see the result using the following payload: &ls
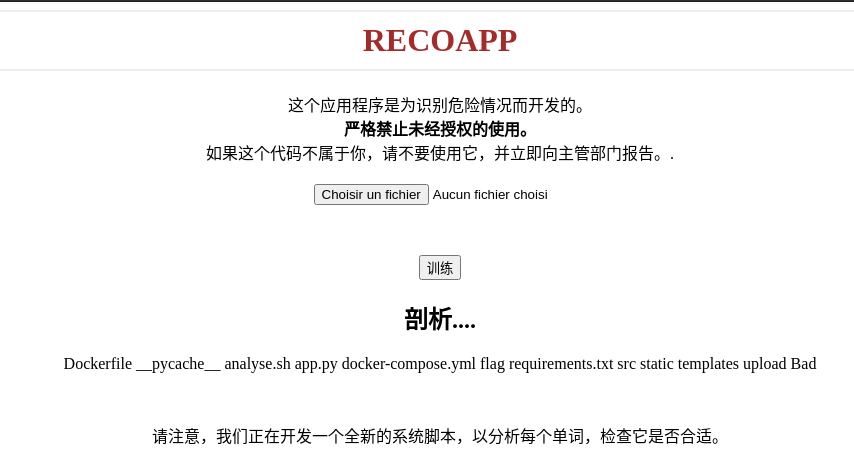
All we need to do is display the result by sending an image containing the text &cat flag.
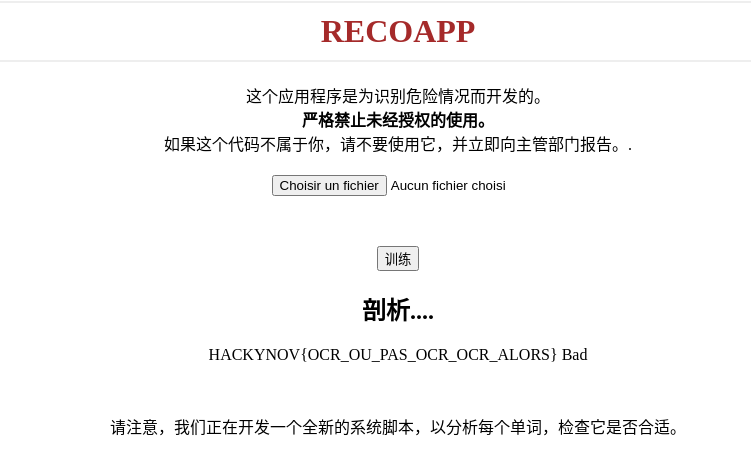
Source
You can find the sources for my challenges here: https://github.com/LOLOLEKIK/hackynov2022